Here's What an Eavesdropper Sees When You Use an Unsecured Wi-Fi Hotspot
Posted: July 30, 2013
[caption id="attachment_11463" align="alignright" width="580"] image from PCWorld[/caption]You’ve probably read at least one story with warnings about using unsecure public Wi-Fi hotspots, so you know that eavesdroppers can capture information traveling over those networks. But nothing gets the point across as effectively as seeing the snooping in action. So I parked myself at my local coffee shop the other day to soak up the airwaves and see what I could see.
image from PCWorld[/caption]You’ve probably read at least one story with warnings about using unsecure public Wi-Fi hotspots, so you know that eavesdroppers can capture information traveling over those networks. But nothing gets the point across as effectively as seeing the snooping in action. So I parked myself at my local coffee shop the other day to soak up the airwaves and see what I could see.
[caption id="attachment_11463" align="alignright" width="580"] image from PCWorld[/caption]You’ve probably read at least one story with warnings about using unsecure public Wi-Fi hotspots, so you know that eavesdroppers can capture information traveling over those networks. But nothing gets the point across as effectively as seeing the snooping in action. So I parked myself at my local coffee shop the other day to soak up the airwaves and see what I could see.
image from PCWorld[/caption]You’ve probably read at least one story with warnings about using unsecure public Wi-Fi hotspots, so you know that eavesdroppers can capture information traveling over those networks. But nothing gets the point across as effectively as seeing the snooping in action. So I parked myself at my local coffee shop the other day to soak up the airwaves and see what I could see.
My intent wasn't to hack anyone's computer or device—that's illegal—but just to listen. It’s similar to listening in on someone’s CB or walkie-talkie radio conversation. Like CBs and walkie-talkies, Wi-Fi networks operate on public airwaves that anyone nearby can tune into.
As you'll see, it’s relatively easy to capture sensitive communication at the vast majority of public hotspots—locations like cafes, restaurants, airports, hotels, and other public places. You can snag emails, passwords, and unencrypted instant messages, and you can hijack unsecured logins to popular websites. Fortunately, ways exist to protect your online activity while you’re out-and-about with your laptop, tablet, and other Wi-Fi gadgets. I'll touch on those, too.
Capturing webpages
I opened my laptop at the coffee shop and began capturing Wi-Fi signals, technically called 802.11 packets, with the help of a free trial of a wireless network analyzer. The packets appeared on screen in real time as they were captured—much more quickly than I could read them—so I stopped capturing after a few minutes to analyze what I had vacuumed up. Note: You can click on any of these screenshots to view larger versions that are easier to read.
[caption id="attachment_11465" align="alignleft"]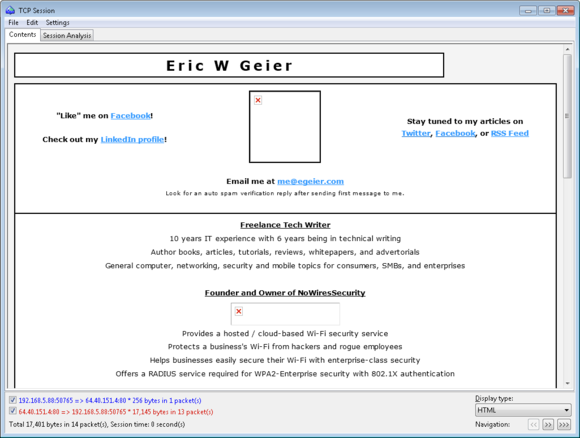 My own website, captured via the hotspot packets and reassembled for viewing.[/caption]I first searched for packets containing HTML code, to see which websites other hotspot users were browsing. While I did see activity from other patrons, I didn’t capture anything interesting, so I visited my own website—www.egeier.com—on my smartphone.
My own website, captured via the hotspot packets and reassembled for viewing.[/caption]I first searched for packets containing HTML code, to see which websites other hotspot users were browsing. While I did see activity from other patrons, I didn’t capture anything interesting, so I visited my own website—www.egeier.com—on my smartphone.
The raw packets with HTML code looked like gibberish, but as you can see above, the trial network analyzer I used reassembled the packets and displayed them as a regular webpage view. The formatting was slightly off and some of the images were missing, but plenty of information still came through.[caption id="attachment_11467" align="alignright"]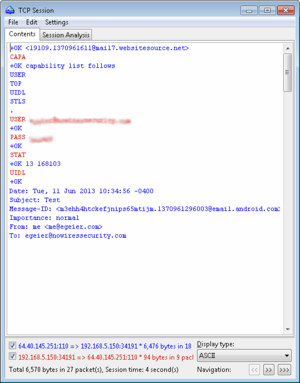 This is a copy of the email I sent (and subsequently received) using my smartphone connected to the hotspot.[/caption]
This is a copy of the email I sent (and subsequently received) using my smartphone connected to the hotspot.[/caption]
I didn’t find anyone else sending or receiving emails during my visit, but I did discover the test messages I sent and received via my smartphone while it was connected to the hotspot. Since I use an app to connect to my email service via POP3 without encryption, you could have seen my login credentials along with the message (I've blurred the username and password in the screenshot).
This is all the information someone would need to configure their email client to use my account and start receiving my emails. They might also be able to send emails from my account.
I also used Yahoo Messenger to send a message while I was capturing Wi-Fi signals. Sure enough, the tool plucked that information out of the air, too. You should never use an unencrypted instant-messaging service with any expectation of privacy.
Read the entire article Here's What an Eavesdropper Sees When You Use an Unsecured Wi-Fi Hotspot, at PCWorld.